3.2 KiB
3.2 KiB
| obj | website | ||
|---|---|---|---|
| os |
|
QubesOS
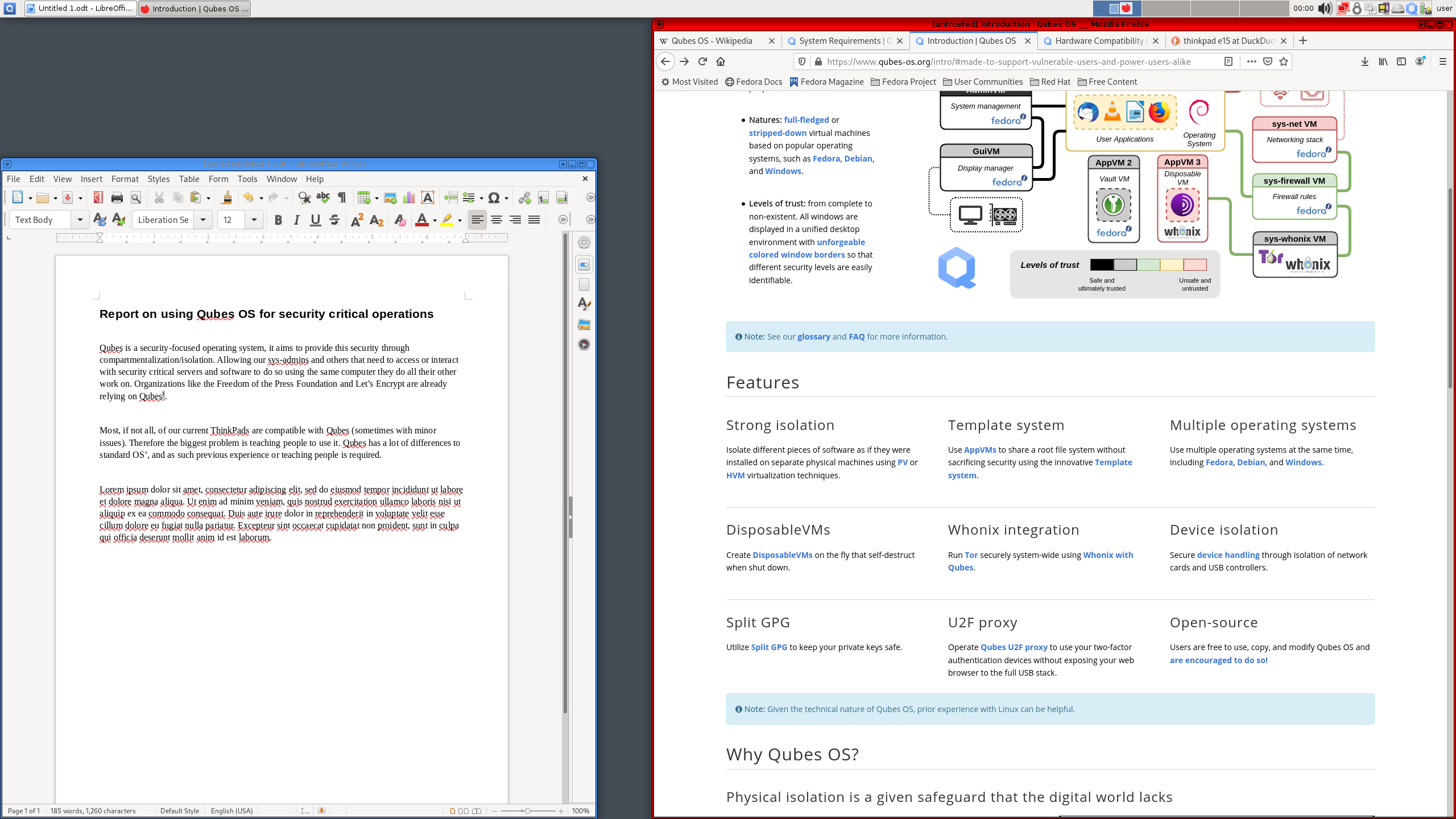
Qubes OS is an open-source, security-focused operating system that prioritizes compartmentalization and isolation to enhance user privacy and security. Qubes OS implements the concept of "security by compartmentalization," where different activities or tasks are separated into distinct virtual machines (VMs) to mitigate the impact of security breaches.
Key Features
1. Security by Compartmentalization:
- Qubes OS uses Xen-based virtualization to create and manage isolated compartments called Qubes. Each Qube serves a specific purpose, and compromising one Qube does not affect the others.
2. AppVMs and Disposable VMs:
- Qubes introduces the concept of AppVMs, which are VMs dedicated to specific tasks or applications. Disposable VMs are short-lived VMs used for temporary tasks, providing enhanced security.
3. Whonix Integration:
- Qubes integrates with Whonix, a privacy-focused operating system, to provide a secure and anonymous environment for browsing and communication.
4. Inter-VM Communication:
- Qubes implements secure inter-VM communication using a mechanism called the Qubes RPC (Remote Procedure Call) system, allowing controlled data exchange between Qubes.
5. TemplateVMs:
- TemplateVMs serve as base systems for AppVMs, allowing for centralized updates and changes that can be easily applied to multiple VMs.
6. Secure Boot and Kernel Isolation:
- Qubes OS leverages secure boot and kernel isolation techniques to enhance the integrity of the system.
Getting Started
1. Installation:
- Follow the installation guide to set up Qubes OS on your hardware. Qubes OS supports a variety of devices, and installation is well-documented.
2. Configuration:
- During the installation process, configure your Qubes OS settings, including disk partitioning, template VMs, and networking options.
3. AppVM Creation:
- After installation, create AppVMs for specific purposes such as work, personal use, or secure browsing.
4. TemplateVM Updates:
- Regularly update TemplateVMs to ensure that all AppVMs based on them receive the latest security patches and updates.
5. Backup and Restore:
- Use the built-in backup and restore features to safeguard your Qubes OS configuration and data.
Usage
1. AppVM Interaction:
- Launch and interact with AppVMs for various tasks. Each AppVM operates independently, enhancing security and privacy.
2. Disposable VMs:
- Use Disposable VMs for tasks that require a temporary and clean environment, such as opening untrusted documents or visiting unknown websites.
3. Secure Browsing with Whonix:
- Utilize Whonix for anonymous and secure web browsing, leveraging the power of the Tor network.
4. Inter-Qube Communication:
- Manage inter-Qube communication carefully, leveraging the Qubes RPC system to control data exchange between Qubes.
5. TemplateVM Maintenance:
- Regularly update and maintain TemplateVMs to keep the entire system secure and up-to-date.